Security Policy
Infinidat: Understanding the Impact of Comprehensive Data Security
Pure Storage FlashArray Security and Compliance
Western Digital. Keep Data Storage Costs Contained While Meeting Security, Control and Governance Objectives
Highlights
- • Scalable storage, for modern and legacy applications, for your data center
- • Multi-cloud access and cross-cloud migration – drag-and-drop files and folders
- • Single pane to establish controls across on-premises and cloud data
- • Data security features and governance with audit controls and monitoring
- • Sensitive data discovery to notify and apply controls for regulatory requirements
- • File sync & share in-house, under your control
- • Interoperability of object and file-based protocols – names and content preserved
- • Transfer acceleration of large files through parallel streaming
- • Web, desktop, mobile apps and office plugins allow access from anywhere
- • WebDAV, FTP, SFTP or mount for application access to storage from any location
Challenges
- • Data Silos – Company data is proliferating across different systems, geographies and vendors – according to one survey on average there are 6.3 ‘file silos’ per user with 76% saying that finding files is painful.1
- • Compliance – Compelled by regulatory changes, and corporate oversight, companies must ‘know’ what sensitive data they control, where it’s located and how it is used, and then apply appropriate control policies.
- • Data Leakage – A major concern to CIOs is how to protect company data inside, and especially outside, their data center. How can they secure data on employee devices and uploaded to unsanctioned file sharing services?
- • Scaling – Media, machine learning and IoT drive ever larger datasets. This puts pressure on traditional filesystems which are expensive to grow, and on outdated approaches to backup and data availability.
Solution
Western Digital’s ActiveScale™ cloud object storage along with Storage Made Easy’s Enterprise File Fabric™ platform reduce costs, and improve availability and oversight, by moving end-user data off traditional filesystems. ActiveScale provides a cost-effective modern storage system that is scalable, durable and fast. The file fabric unifies ActiveScale along with other private and public data stores into a single, centrally managed virtual filesystem, with web, desktop and mobile entry points.
A Powerful solution from Western Digital and Storage Made Easy
The exponential growth of unstructured data has created huge challenges for enterprises and service providers. Storage and compliance costs take an ever-growing slice of the budget as companies manage petabytes and even exaabytes of data while also dealing with increased regulatory oversight. How can organizations keep data costs contained while tackling the regulatory requirements from GDPR and other new privacy regulations?
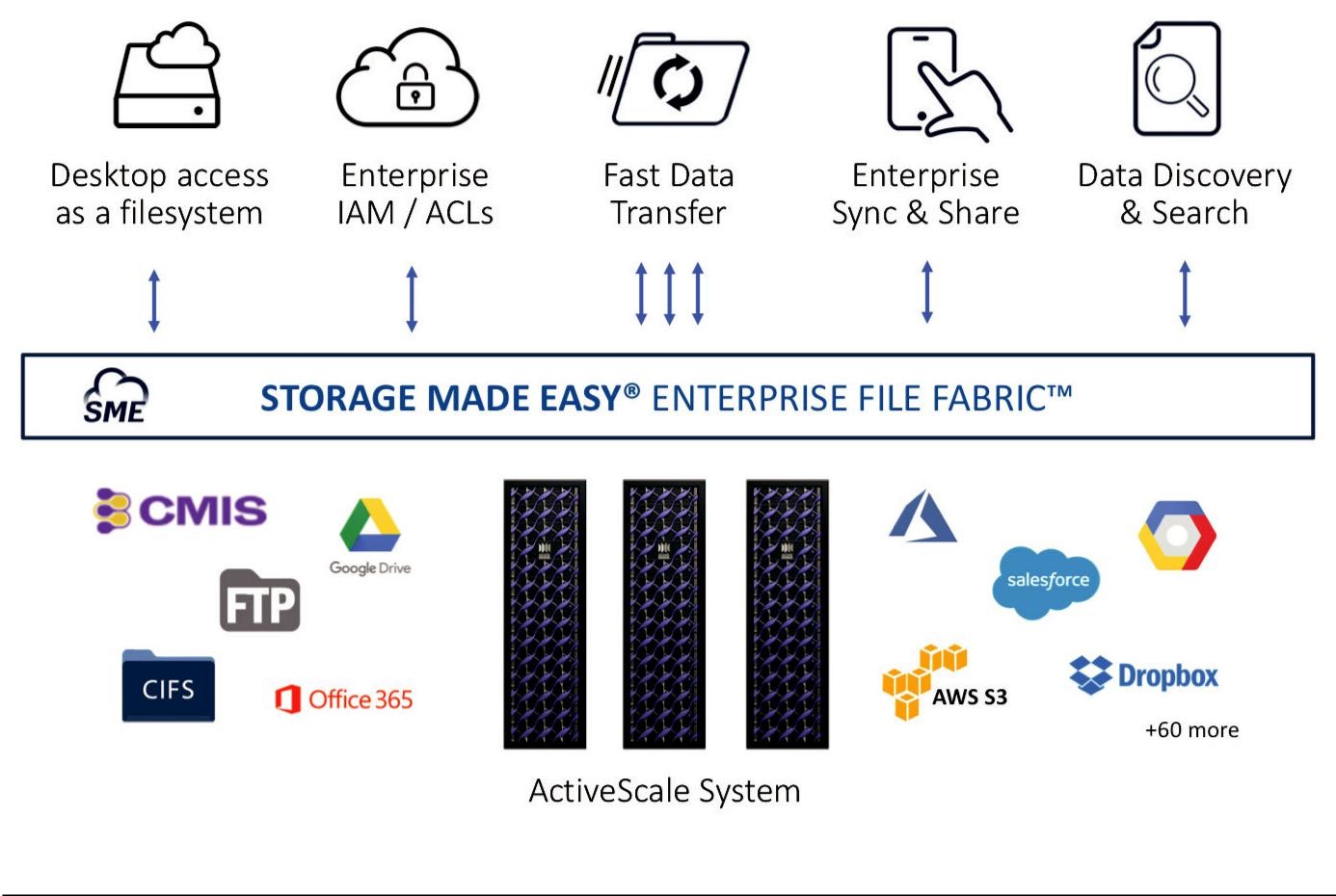
Storage Made Easier
- • Anywhere Access Anytime
The same data can be read and edited at corporate, in remote offices, cafes and on mobile devices. Files can be synced to desktop and mobile devices to work offline. A complete suite of desktop (MacOS®, Windows®, Linux®), mobile (Android™, iOS) and app plugins (Office, mail) provides uses access to files, sharing tools and management controls.
- • Enterprise File Services
The File Fabric allows the lower cost, scalable ActiveScale to be controlled and used as easily as a filesystem. Adding locking, versioning, renaming and a trash bin, users can access data using familiar tools and their existing desktop applications. Collaboration tools for internal and external users include the ability to create share links with download limits, expiration dates and 2FA (two factor authentication). Document annotation, commenting and approval workflows are also supported.
- • Data Protection Features
Policy-based security controls are applied centrally for all data sources, reducing time and exposure for IT security. Discover potentially sensitive or regulated data moving into ActiveScale, with automated classification and file tagging. Restrict access to authorized users based on ACL, role or classification. Link access control to existing authentication systems such as AD, LDAP, SAML. Create (?) policy-based data sharing, retention and privacy. Full event-based audit reports and monitoring.
- • Cost Savings
ActiveScale cloud object storage system with Storage Made Easy’s Enterprise File Fabric platform provides an incredibly economical file storage platform that doesn’t compromise scalability, reliability or performance.
- • Conclusion
The powerful combination of Western Digital’s ActiveScale cloud object storage with Storage Made Easy’s Enterprise File Fabric platform helps IT organizations and security teams combat cloud data sprawl and shadow IT by introducing an enterprise-wide file fabric that assimilates on-premises and cloud-based resources. Administrators can institute uniform security policies and monitor access across private and public infrastructure from a single vantage point. Users get authorized access to the data they need from anywhere, anytime across virtually any device.
Infinidat: Understanding the Impact of Comprehensive Data Security
2017 was not an easy year to be a CIO or CISO, and 2018 isn’t showing any signs of being easier. With so many career-ending-level data breaches in 2017 (e.g.Equifax, Uber, Yahoo to name a few) and with the stronger regulatory requirements worldwide, CIOs / CISOs have a corporate responsibility to rethink their approach to data security. Regulatory compliance aside, companies have a responsibility to their customers and shareholders to protect data, and minimize its exposure not only to external attackers but also to employees. The most common method of data breach in 2017 was phishing Email sent to the company’s internal employees (See 2017 Data Breach Investigation Report), This makes the employees unwillingly complicit in the data breach. Over 80% of successful cyber attacks have a critical human element that enabled them. The average-employee who opens the innocent-looking attachment or link, unintentionally jeopardizing the company's data. While there is no 100% protection”, there are common sense rules to decrease the attack surface of any company.
There are 2 terms we need to keep in mind when thinking about protecting data from hackers:
“The attack surface of a software environment is the sum of the different points (the “attack vectors”) where an unauthorized user (the “attacker”) can try to enter data to or extract data from an environment. Keeping the attack surface as small as possible is a basic security measure.” (Wikipedia)
A corporation that treats its data as the source of its business advantage, and understands how sensitive it is to its customers, how should it minimize the attack surface, and why are AFAs (All Flash Arrays) in the way of this?
When the org-chart dictates the security method
Conway’s law has long taught us that the organizational structure directly impacts the results / design more than anything else. In the context of security this is fairly simple: If the CISO and storage manager are highly coordinated in their work, you are going to find your data encrypted in the storage layer, and the “encryption” box will be checked. Storage is also the “path of least resistance” as storage arrays can instantly enable encryption without any performance penalty. However, is storage level encryption helping to reduce your attack surface? A little, yes. It still leaves ALL other layers unencrypted, and that data traverses the network unprotected.
So where should we encrypt the data?
Think of it this way - the higher up the encryption of personal / sensitive data happens, the more layers remain protect. Each row in the table below represents your attack surface if you choose a specific layer to encrypt the data in.
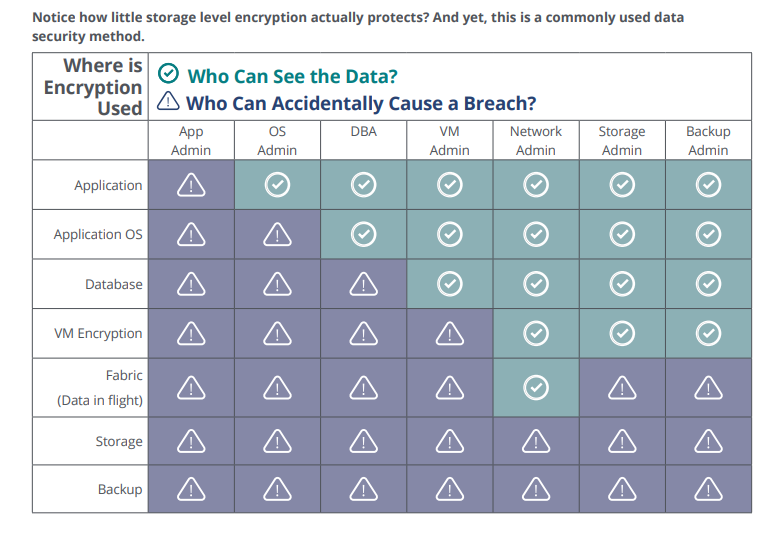
Notice how little storage level encryption actually protects?
And yet this is a commonly used data security method.
Why Are All-Flash-Arrays Increasing Your Attack Surface?
While most (if not all) AFAs offer disk level encryption, that is the only level of encryption they allow—data is encrypted anywhere else, the AFAs can’t perform data reduction and the entire economics of AFAs break. AFAs must rely on data reduction (1:3 and 1:6) to minimize the price premium to a point where the customers can afford it. This means customers choosing to base their production infrastructure on All-Flash-Arrays are effectively blocking themselves from implementing an end-to-end encryption policy, which all regulations of data privacy require (GDPR, SB-1386, HIPAA, PCI-DSS, NY-DFS and others).
When “Optimal” Meets Feasible
This optimal approach for data security is often limited by pre-existing realities:
The 10-year-old application that doesn’t offer encryption and is no longer support
The business critical app that takes a year to receive maintenance for
The application owner who won’t invest the time to encrypt
When the rubber hits the road, compromises are often needed to accelerate your data security adoption. Many customers will opt to encrypt these environments in lower levels of the stack (DB/VM/OS) to be able to comply with corporate and regulatory requirements. This approach is often mandatory to meet compliance deadlines, however it’s worth limiting the number of separate approaches the company uses to avoid a high overhead. It’s worth noting (again) that all these alternatives have the same effect—limiting the data reduction of AFAs, and increasing their storage TCO.
Additional Benefits of Encrypting up the Stack
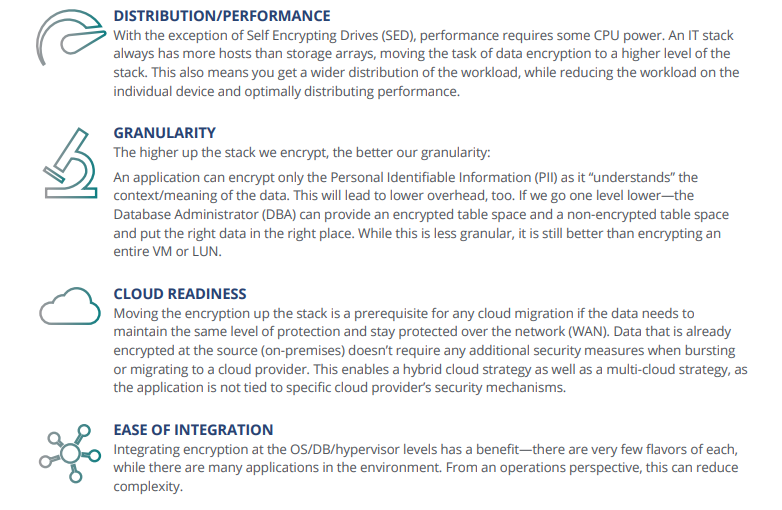
Call to Action
- • Plan your organization’s holistic data protection policy
- • Set a cut-off date for new applications to be designed with encryption from day one
- • Train in-house application developers on security-by-design methodologies
- • Examine existing applications looking for the right way for your organization to protect data-in-flight
- • Build a transition plan to encrypt legacy applications with private or sensitive data
Pure Storage FlashArray Security and Compliance
There is no doubt that data security is an increasingly critical concern for organizations worldwide. Lack of effective technology and weak security policies can leave an organization open to liability. One of the drawbacks to improving security is the perceived administrative overhead associated with doing so. An organization must weigh new processes and technologies with all of the new complexity in securing and managing that data. Within the industry there is an expectation of friction between ease of administration and implementation of comprehensive data security, which can be a barrier organizations must overcome. Or, alternatively, they must find a way a better way to get the results they desire.
Pure Storage believes that data needs to be secured to the highest possible standards, and that this level of security should be transparent to customers. By transparent, we mean invisible to the customer and requiring zero management. Pure Storage® accomplishes this by securing data at rest with AES-256 bit encryption. Moreover, our data encryption occurs without impact to performance and while maintaining full data reduction capabilities. Pure Storage FlashArray encryption is FIPS 140-2 certified, NIST compliant, NIAP/Common Criteria validated, and PCI-DSS compliant. The efficacy of our data encryption and data erasure have been validated by Kroll OnTrack, one of the industry’s leading security firms.
With the increase in data protection and compliance regulations required by various industries, countries and regions, the high level of built-in security and encryption capability available in a FlashArray represents an effective way to help achieve data protection regulatory compliance. To see how FlashArray can contribute to the European Union’s General Data Protection Regulation, read our report, FlashArrays and GDPR Compliance.
Achieving high levels of security does not equate to product complexity – Pure Storage FlashArray encryption at rest is protected by an internal process that removes key management from users. Not only does this allow our customers to focus on data storage, it also removes human error from the process. Our key management is sophisticated, including automatic key rotation, periodic key regeneration, and unreadable partitioned keys that are spread over FlashArray flash modules. In the event of total array loss, multiple steps are required to reconstruct the data, requiring physical access to a majority of the modules of the array, access to all secure keys that are partitioned across all flash modules, and a deep understanding of the hidden logical structure of the internal databases.
To completely lock down the array, even in the event of total loss to a highly-skilled intruder with deep product-specific knowledge, Pure Storage also provides Rapid Data Locking through two optional external key technologies:
- • USB connected Spyrus Rosetta II Smartcards. A FlashArray can be completely locked (data rendered permanently unrecoverable) with the removal of the smart card and power loss to the array
- • KMIP (Key Management Interoperability Protocol) remote key server. A FlashArray can be locked down by revoking a remote key and powering off the FlashArray.
About Data at Rest Encryption
The FlashArray encrypts data with the use of three dependent layers of internal keys:w an Array Key (figure 1), an SSD Key (figure 2), and a Data Encryption Key (figure 3).
The array key is generated with a random secret and then broken up over a number of SSDs. This method assures that half of the array drives, plus two more, are required to recreate the current access keys. SSD keys are never exposed on any array interface, nor does any single SSD contain a full encryption key.
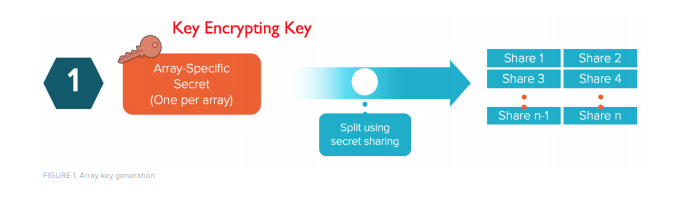
Array Key (key encrypting key)
- • Created at array initialization
- • Distributed across SSDs using “secret sharing” algorithm
- • Changed every 24 hours, and when there are configuration changes
When a flash module needs to be replaced, it is inserted into the array and initialized. At this point, a device-specific access key is created and sent to the device. The FlashArray must supply the access keys to unlock any flash module – and once the device key is written to the flash module, it cannot be read back. These various flash module access keys are only accessible with the Array key.
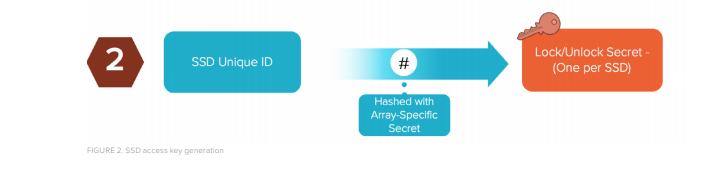
SSD Access Key (unlock key)
- • Generated at boot with hash of Array Key and SSD Key
- • Unique per device (NVRAM and SSD)
- • Cannot not be read back
Finally, the array uses a data encryption key to encrypt data stored on flash modules. Like the SSD access key, the encryption key is also partitioned across all of the devices. An array’s data encryption key is constant for the life of the array, but it is re-encrypted each time the array creates new device access keys. Like SSD access keys, array data encryption keys cannot be exposed or read back.
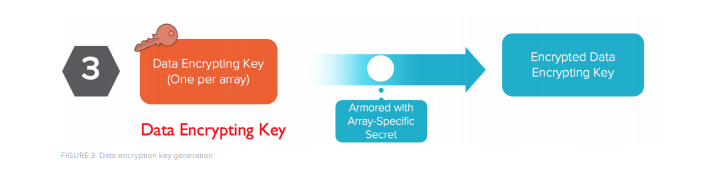
Data Encryption Key
- • Requires unlocked SSDs since it is stored and partitioned on the SSD itself
- • Cannot be read back like the SSD Key
- • Armored by Array Key using a AES256 Key wrap
The Array Key expires every 24 hours – this is required to unlock the flash modules, which have a unique ID that must match the FlashArray to device hash. Once a quorum of drives are unlocked (half of the drives plus two), only then can the Data Encrypting Key be read. This process runs continuously in the background, assuring that no single device, or even half of the devices, can allow data access.
RAPID DATA LOCKING (RDL)
Some environments require external key management for locking down an array that is forward deployed. There are two solutions:
- 1. USB connected Smartcards
- 2. KMIP connectivity for remotely managed keys
Smartcard RDL
With Smartcard RDL, customer-programmable Spyrus Rosetta II Smartcards act as security tokens that enhance SSD access keys and participate in key regeneration at power-on. Once unlocked, flash modules are accessible, but when smartcards are removed from the USB connected readers, the SSDs cannot be unlocked at power-on. For example, if an array is transported separately from its smartcards, data on its SSDs cannot be read or written, even with specific Pure Storage knowledge and the required skills in cryptography. The smart cards act as a secondary SSD key, and without access to them, none of the flash modules can be unlocked.
KMIP RDL
Conceptually, KMIP RDL works the same way – a secondary user-controllable key is introduced that allows for unlocking the array’s flash modules. Instead of being physically connected to the array through a USB card reader, KMIP keys are remotely accessed from a KMIP server. Without access to the server, the flash modules cannot be unlocked on power-on.
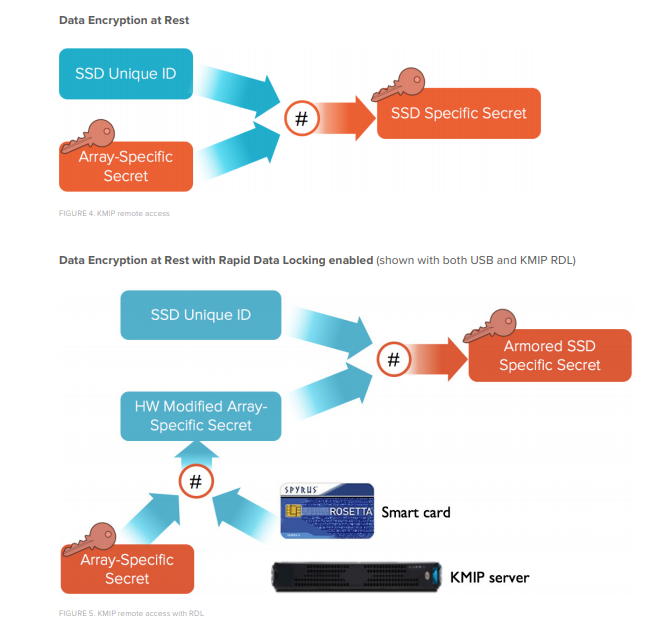
RDL can be enabled during installation, or at any time thereafter. Once enabled, RDL is permanent. It applies to all of an array’s SSDs, including those added afterward.
COMPLIANCE AND CERTIFICATION
The FlashArray is FIPS 140-2 certified, Common Criteria certified, and PCI-DSS compliant. The following are the NIST validations for the algorithms used for encryption.
AES [FIPS 197 and SP 800-38A]
AES: http://csrc.nist.gov/groups/STM/cavp/documents/aes/aesval.html Validation nr. 3181
[FIPS 198-1]
HMAC: http://csrc.nist.gov/groups/STM/cavp/documents/mac/hmacval.html Validation nr. 2007
[FIPS 180-4]
SHS: http://csrc.nist.gov/groups/STM/cavp/documents/shs/shaval.htm Validation nr. 2633
[FIPS 140-2 Certification]
https://csrc.nist.gov/projects/cryptographic-module-validation-program/Certificate/2467
NIAP Certification (with Purity 4.7+ )
https://www.niap-ccevs.org/st/Compliant.cfm?pid=10664
Common Criteria (CC) Information
The Common Criteria Recognition Arrangement (CCRA) is an international agreement that defines criteria for specifying and evaluating security in information technology products.
Strict CC compliance requires certain Pure Storage FlashArray capabilities – for example, PhoneHome and RemoteAssist – be restricted. These features can be enabled, but full relaxation of Common Criteria compliance would require Technical Support engagement.
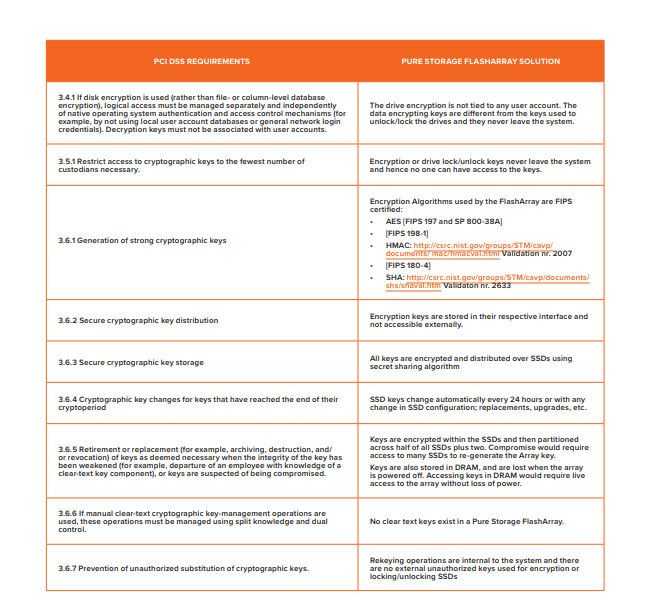
Payment Card Industry Data Security Standard (PCI-DSS)
PCI-DSS is a standard for managing credit card information of customers. It defines rules of security for various data center devices.
PCI-DSS specifies a number of requirements which are met or exceeded by criteria in the Pure FlashArray Common Criteria certification.
Summary
Pure Storage, with a continuous emphasis on simplicity, has implemented rigorous security measures including AES256 bit encryption, data erasure, rapid data locking technologies, key management, and a robust encrypt/decrypt process. These features meet or exceed internationally recognized security standards such as FIPS 140-2, NIAP/ Common Criteria and PCI-DSS. Coupled with comprehensive organizational security measures, FlashArray can help customers meet security requirements and data compliance regulations around the world – including the recently updated GDPR. Pure Storage has achieved this without compromise in product serviceability, performance, or our industry leading data reduction capabilities